Excuse the ads! We need some help to keep our site up.
List
Conditions
- 해당 기술은 다음과 같은 조건에서 동작합니다.
- 공격자에 의해 Heap 영역을 할당, 해제를 할 수 있어야 합니다.
- 공격자에 의해 해제된 영역의 크기와 같거나 작은 영역을 할당 할 수 있어야 합니다.
Exploit plan
- 다음과 같은 방법으로 공격할 수 있습니다.
- 2개의 Heap 영역을 할당합니다.
- 1개의 Heap 영역을 해제합니다.
- 힙 영역을 할당합니다.
- Fast bin
- 해제된 Chunk가 fastbinsY에서 관리될 경우 해제된 Heap의 크기와 동일하게 할당합니다.
- Small, Large chunk
- 해제된 Chunk가 Unsorted bin에서 관리될 경우 해제된 Heap의 크기와 같거나 작은 크기를 할당합니다.
- Fast bin
- 해제되었던 영역을 재할당 받습니다.
Example
Files
Source code
Source code
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
int main()
{
char* a = malloc(160);
char* b = malloc(256);
char* c;
free(a);
c = malloc(144);
strcpy(c, "Secret message");
printf("%s\n",a);
}
Exploit flow
first-fit(Use-After-Free)
Debugging
- 다음과 같이 Break point를 설정합니다.
- 0x4005e8 : free() 함수 호출
- 0x4005f7 : malloc(144) 함수 호출
- 0x400629 : leave 명령어
Break points
gdb-peda$ b *0x00000000004005e8 Breakpoint 1 at 0x4005e8 gdb-peda$ b *0x00000000004005f7 Breakpoint 2 at 0x4005f7 gdb-peda$ b *0x0000000000400629 Breakpoint 3 at 0x400629 gdb-peda$
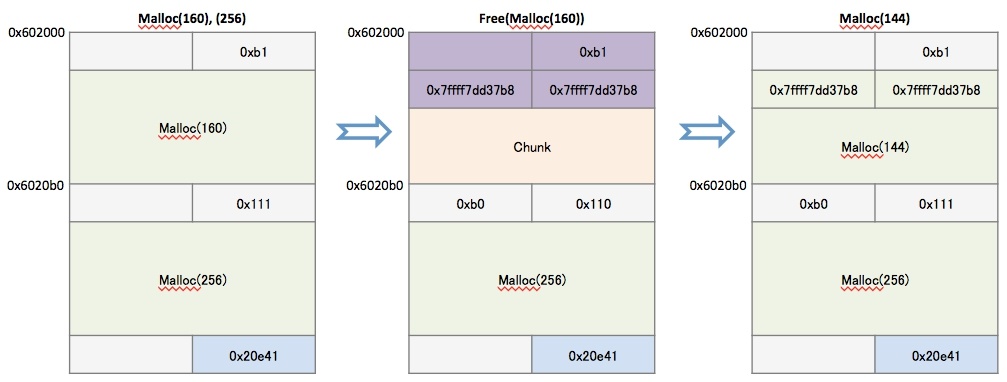
- 다음과 같이 할당된 Heap 영역을 Unsorted bin에 등록할 수 있습니다.
- 해당 프로그램에 할당된 Heap 영역은 다음과 같습니다.
- 첫번째 Heap 영역 : 0x602010
- 두번째 Heap 영역 : 0x6020c0
- free()가 호출된 후에 Unsorted bin에 0x602000 이 등록되었습니다.
- 해당 프로그램에 할당된 Heap 영역은 다음과 같습니다.
Break point - 0x4005e8
gdb-peda$ r Starting program: /home/lazenca0x0/Documents/def/first_fit Breakpoint 1, 0x00000000004005e8 in main () gdb-peda$ x/60gx 0x602000 0x602000: 0x0000000000000000 0x00000000000000b1 0x602010: 0x0000000000000000 0x0000000000000000 0x602020: 0x0000000000000000 0x0000000000000000 0x602030: 0x0000000000000000 0x0000000000000000 0x602040: 0x0000000000000000 0x0000000000000000 0x602050: 0x0000000000000000 0x0000000000000000 0x602060: 0x0000000000000000 0x0000000000000000 0x602070: 0x0000000000000000 0x0000000000000000 0x602080: 0x0000000000000000 0x0000000000000000 0x602090: 0x0000000000000000 0x0000000000000000 0x6020a0: 0x0000000000000000 0x0000000000000000 0x6020b0: 0x0000000000000000 0x0000000000000111 0x6020c0: 0x0000000000000000 0x0000000000000000 0x6020d0: 0x0000000000000000 0x0000000000000000 0x6020e0: 0x0000000000000000 0x0000000000000000 0x6020f0: 0x0000000000000000 0x0000000000000000 0x602100: 0x0000000000000000 0x0000000000000000 0x602110: 0x0000000000000000 0x0000000000000000 0x602120: 0x0000000000000000 0x0000000000000000 0x602130: 0x0000000000000000 0x0000000000000000 0x602140: 0x0000000000000000 0x0000000000000000 0x602150: 0x0000000000000000 0x0000000000000000 0x602160: 0x0000000000000000 0x0000000000000000 0x602170: 0x0000000000000000 0x0000000000000000 0x602180: 0x0000000000000000 0x0000000000000000 0x602190: 0x0000000000000000 0x0000000000000000 0x6021a0: 0x0000000000000000 0x0000000000000000 0x6021b0: 0x0000000000000000 0x0000000000000000 0x6021c0: 0x0000000000000000 0x0000000000020e41 0x6021d0: 0x0000000000000000 0x0000000000000000 gdb-peda$ p main_arena.bins[1] $1 = (mchunkptr) 0x7ffff7dd37b8 <main_arena+88> gdb-peda$ ni 0x00000000004005ed in main () gdb-peda$ p main_arena.bins[1] $2 = (mchunkptr) 0x602000 gdb-peda$ x/60gx 0x602000 0x602000: 0x0000000000000000 0x00000000000000b1 0x602010: 0x00007ffff7dd37b8 0x00007ffff7dd37b8 0x602020: 0x0000000000000000 0x0000000000000000 0x602030: 0x0000000000000000 0x0000000000000000 0x602040: 0x0000000000000000 0x0000000000000000 0x602050: 0x0000000000000000 0x0000000000000000 0x602060: 0x0000000000000000 0x0000000000000000 0x602070: 0x0000000000000000 0x0000000000000000 0x602080: 0x0000000000000000 0x0000000000000000 0x602090: 0x0000000000000000 0x0000000000000000 0x6020a0: 0x0000000000000000 0x0000000000000000 0x6020b0: 0x00000000000000b0 0x0000000000000110 0x6020c0: 0x0000000000000000 0x0000000000000000 0x6020d0: 0x0000000000000000 0x0000000000000000 0x6020e0: 0x0000000000000000 0x0000000000000000 0x6020f0: 0x0000000000000000 0x0000000000000000 0x602100: 0x0000000000000000 0x0000000000000000 0x602110: 0x0000000000000000 0x0000000000000000 0x602120: 0x0000000000000000 0x0000000000000000 0x602130: 0x0000000000000000 0x0000000000000000 0x602140: 0x0000000000000000 0x0000000000000000 0x602150: 0x0000000000000000 0x0000000000000000 0x602160: 0x0000000000000000 0x0000000000000000 0x602170: 0x0000000000000000 0x0000000000000000 0x602180: 0x0000000000000000 0x0000000000000000 0x602190: 0x0000000000000000 0x0000000000000000 0x6021a0: 0x0000000000000000 0x0000000000000000 0x6021b0: 0x0000000000000000 0x0000000000000000 0x6021c0: 0x0000000000000000 0x0000000000020e41 0x6021d0: 0x0000000000000000 0x0000000000000000 gdb-peda$
- 다음과 같이 첫번째 Heap 영역을 다시 할당 받을 수 있습니다.
- malloc(144) 호출 후 리턴된 Heap 영역을 주소는 0x602010 입니다.
- 해당 영역은 앞에서 해제된 첫번째 Heap 영역입니다.
Break point - 0x4005f7
Breakpoint 2, 0x00000000004005f7 in main () gdb-peda$ i r rax rax 0x602010 0x602010 gdb-peda$ x/60gx 0x602000 0x602000: 0x0000000000000000 0x00000000000000b1 0x602010: 0x00007ffff7dd3858 0x00007ffff7dd3858 0x602020: 0x0000000000000000 0x0000000000000000 0x602030: 0x0000000000000000 0x0000000000000000 0x602040: 0x0000000000000000 0x0000000000000000 0x602050: 0x0000000000000000 0x0000000000000000 0x602060: 0x0000000000000000 0x0000000000000000 0x602070: 0x0000000000000000 0x0000000000000000 0x602080: 0x0000000000000000 0x0000000000000000 0x602090: 0x0000000000000000 0x0000000000000000 0x6020a0: 0x0000000000000000 0x0000000000000000 0x6020b0: 0x00000000000000b0 0x0000000000000111 0x6020c0: 0x0000000000000000 0x0000000000000000 0x6020d0: 0x0000000000000000 0x0000000000000000 0x6020e0: 0x0000000000000000 0x0000000000000000 0x6020f0: 0x0000000000000000 0x0000000000000000 0x602100: 0x0000000000000000 0x0000000000000000 0x602110: 0x0000000000000000 0x0000000000000000 0x602120: 0x0000000000000000 0x0000000000000000 0x602130: 0x0000000000000000 0x0000000000000000 0x602140: 0x0000000000000000 0x0000000000000000 0x602150: 0x0000000000000000 0x0000000000000000 0x602160: 0x0000000000000000 0x0000000000000000 0x602170: 0x0000000000000000 0x0000000000000000 0x602180: 0x0000000000000000 0x0000000000000000 0x602190: 0x0000000000000000 0x0000000000000000 0x6021a0: 0x0000000000000000 0x0000000000000000 0x6021b0: 0x0000000000000000 0x0000000000000000 0x6021c0: 0x0000000000000000 0x0000000000020e41 0x6021d0: 0x0000000000000000 0x0000000000000000 gdb-peda$
- 다음과 같이 문자열이 출력됩니다.
- 세번째 할당 받은 Heap 영역에 문자열을 복사했습니다.
- 해제된 첫번째 Heap 영역을 출력하면 세번째 Heap 영역에 복사한 문자열이 출력됩니다.
Break point - 0x400629
gdb-peda$ c Continuing. Secret message Breakpoint 3, 0x0000000000400629 in main () gdb-peda$